Task List
2024.08~
I'm currently working on a COFF parser and an ELF parser, which will be combined with a PE parser.
(I will be adding ELF code obfuscation first, followed by ELF packer, then COFF code obfuscation.)
ELF 0. SRC File
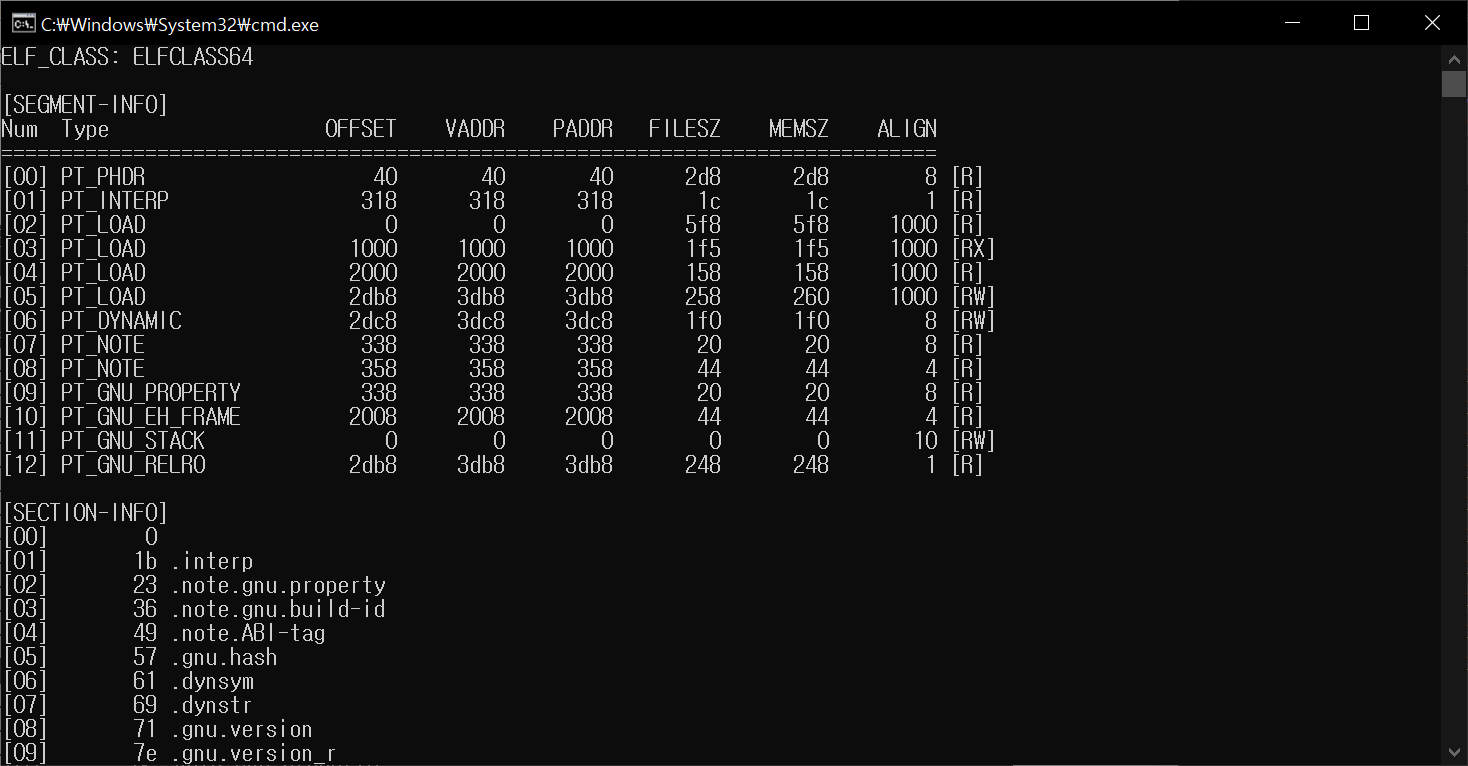
ELF 1. Added Segments
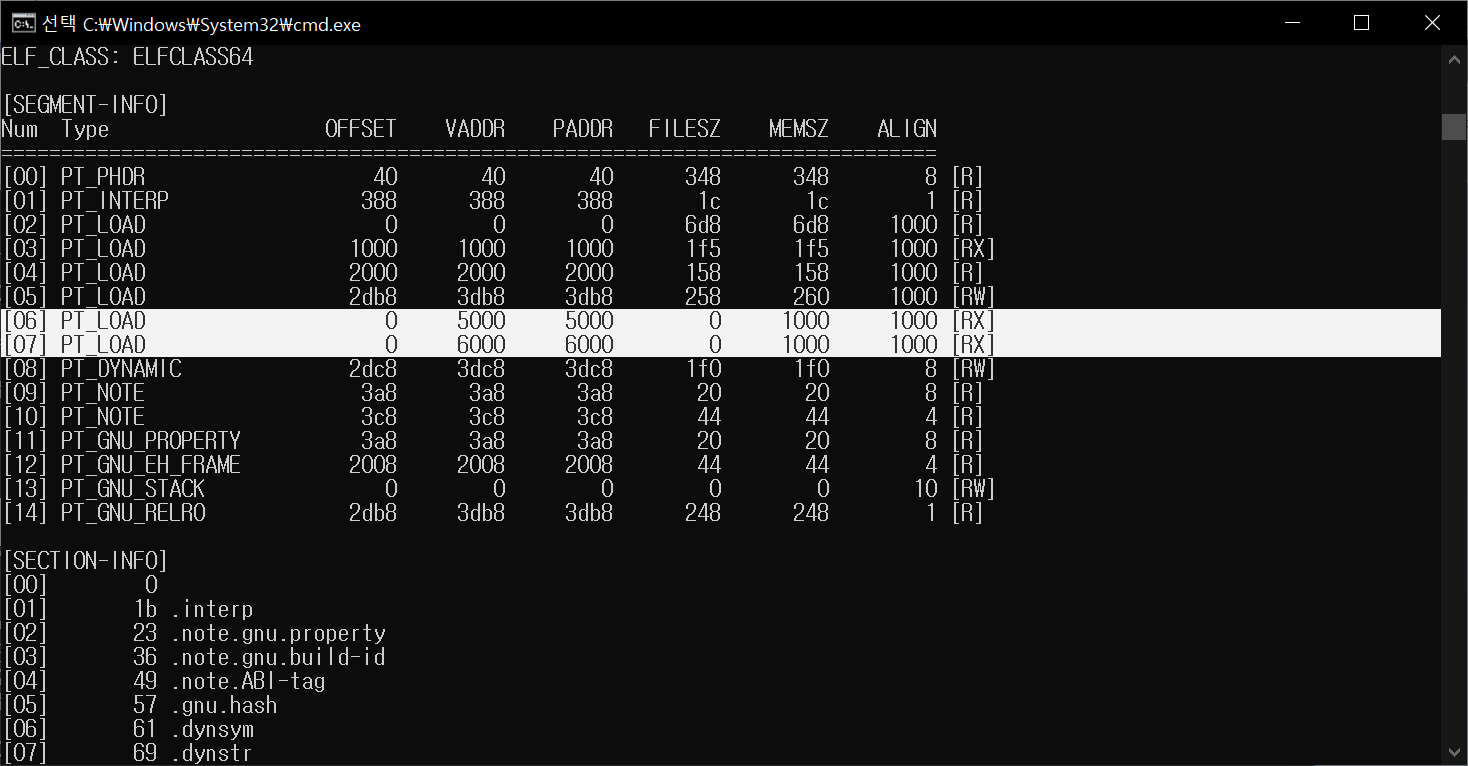
ELF 2. Added Sections
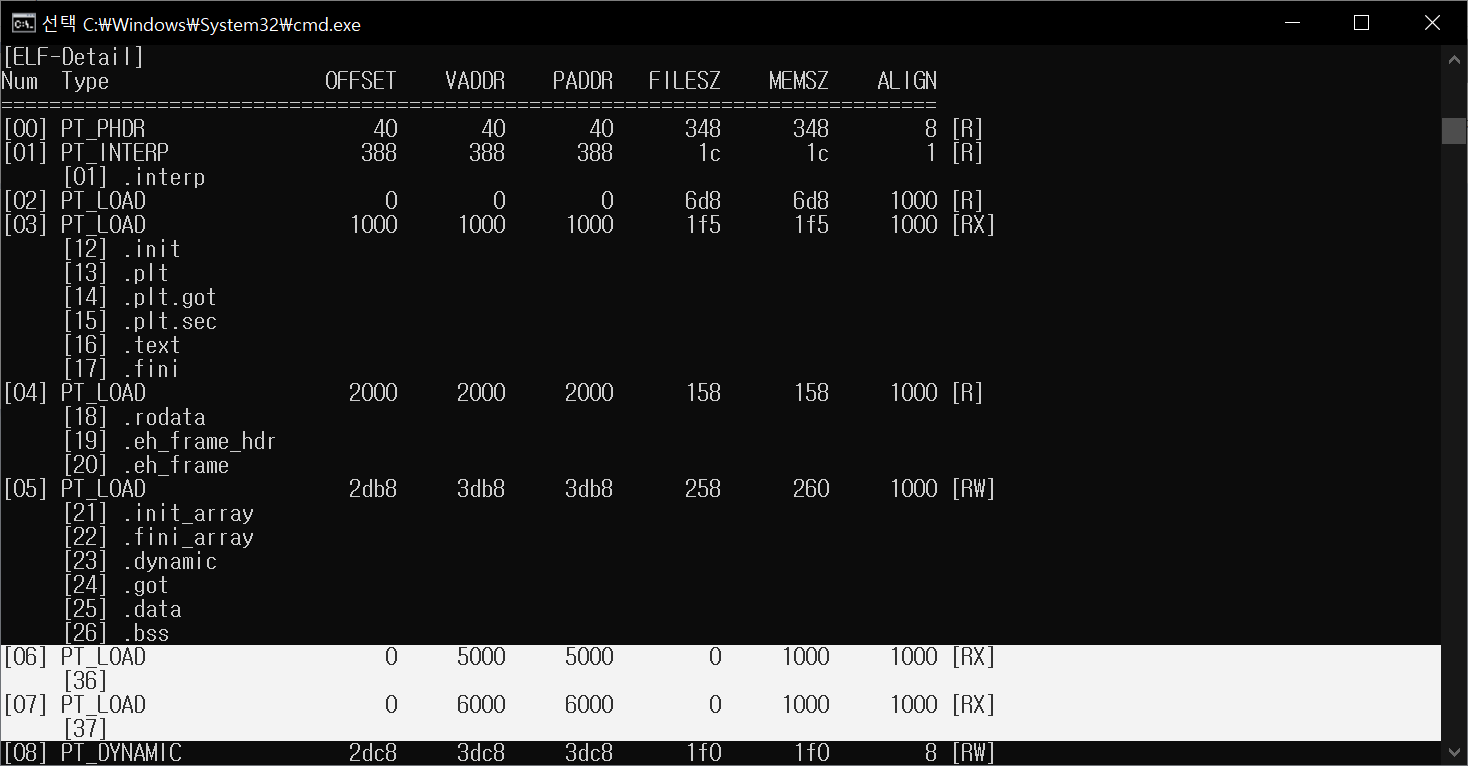
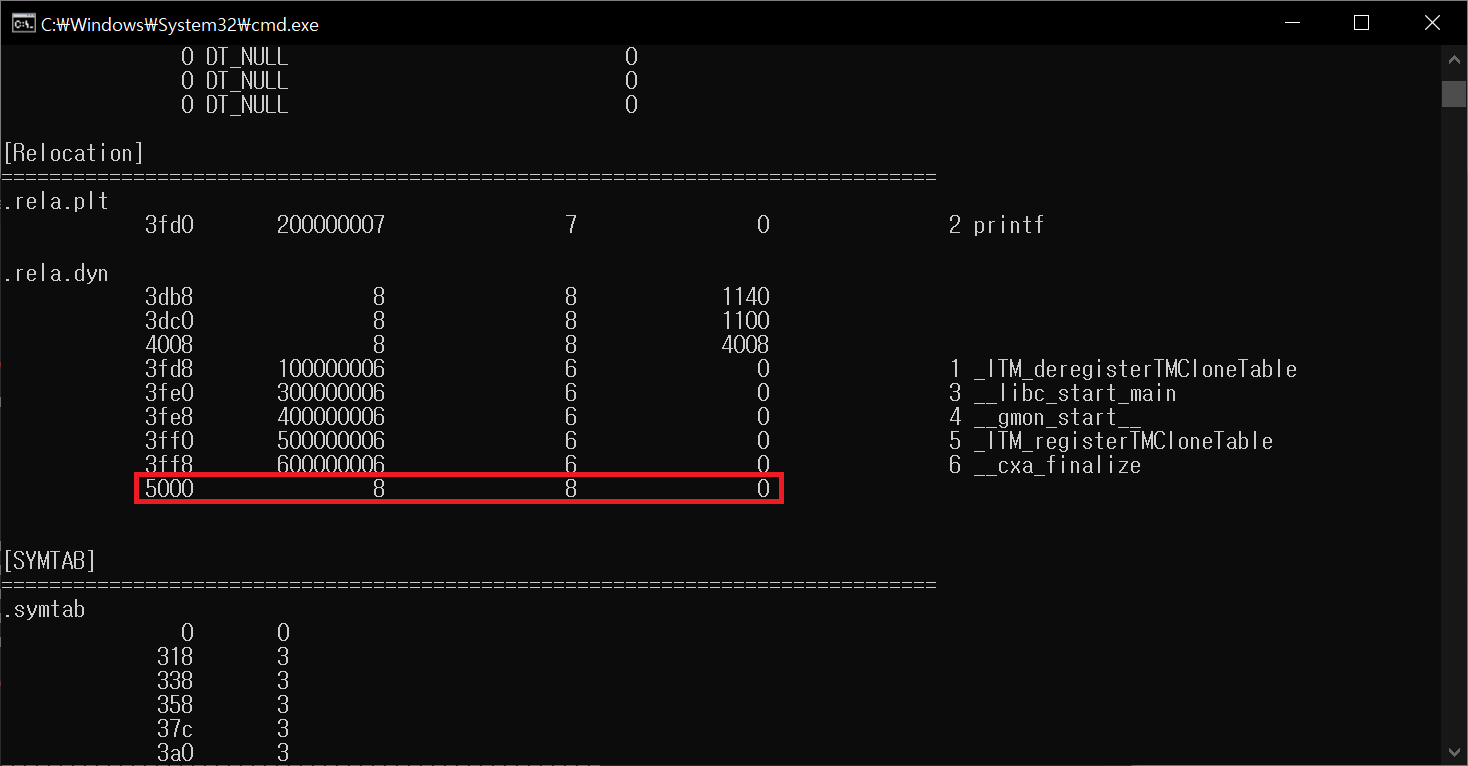
ELF 3. Check Segment and Sections(; image dump sections)
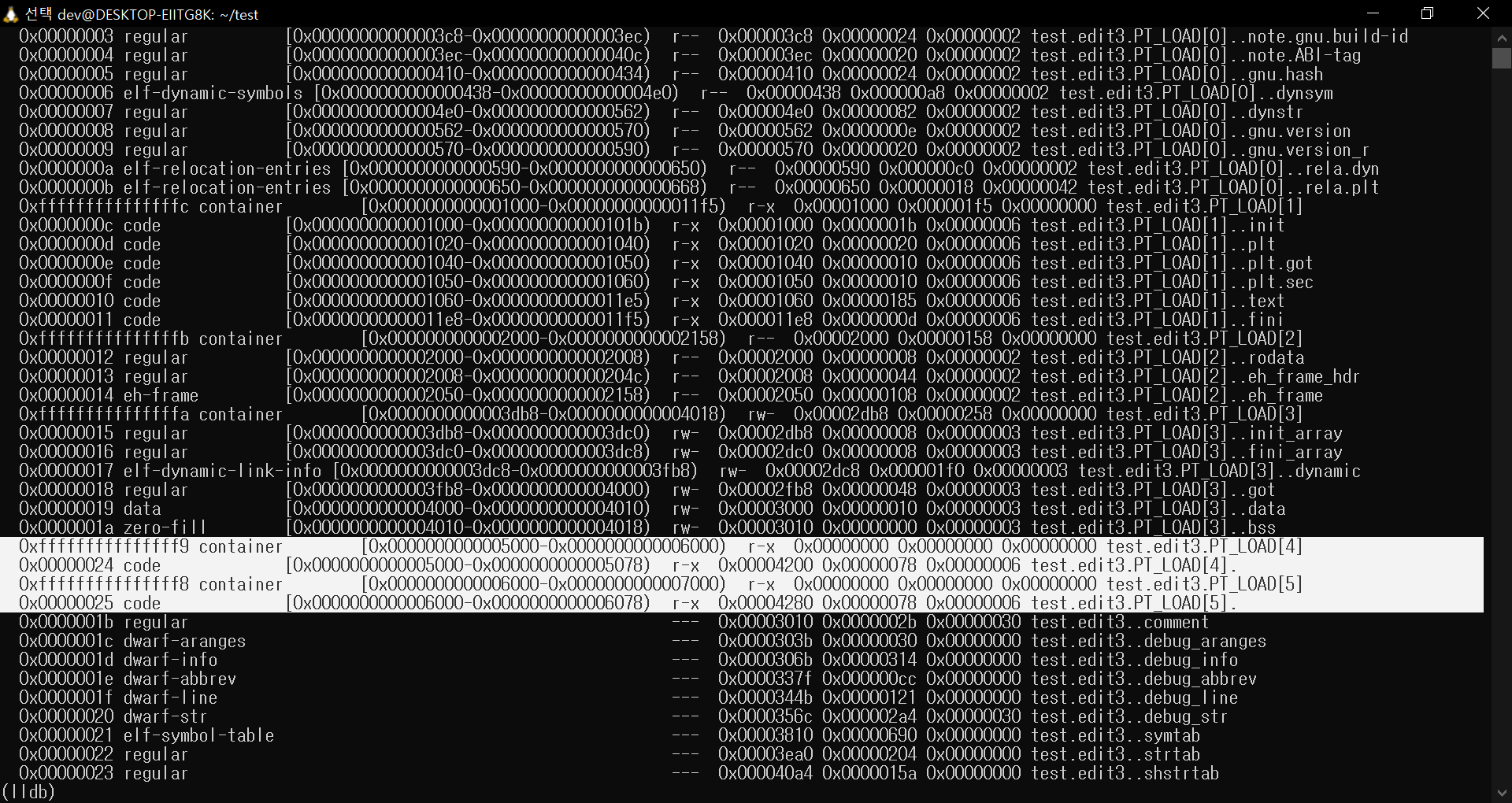
ELF 4. Check Section Data
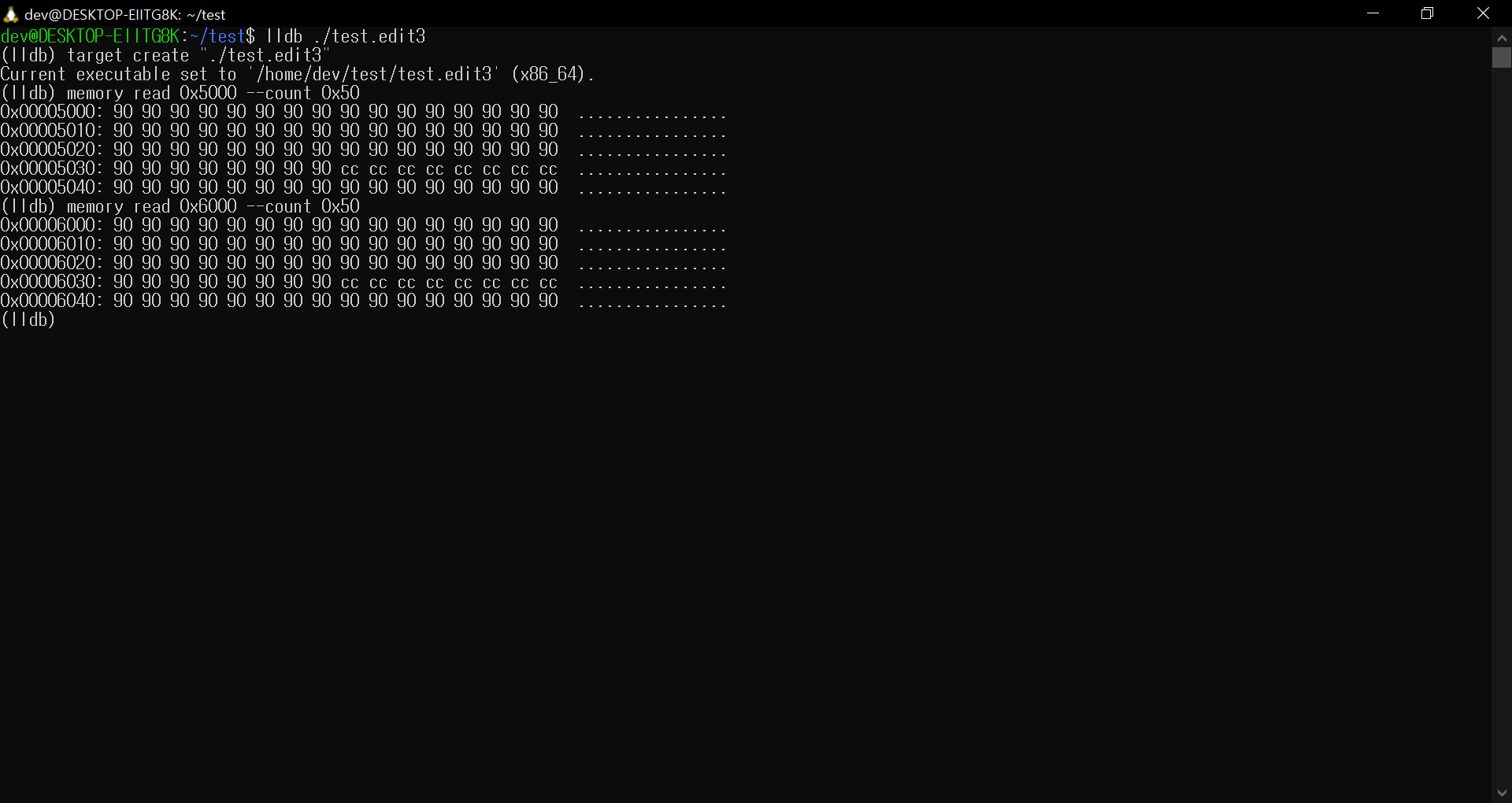
[2024.09.22.update]
I added a disassembler for elf-format, and now I can compute the function to be obfuscated via SDK or symbols.
Now, i'm started porting the code obfuscation tools.
---
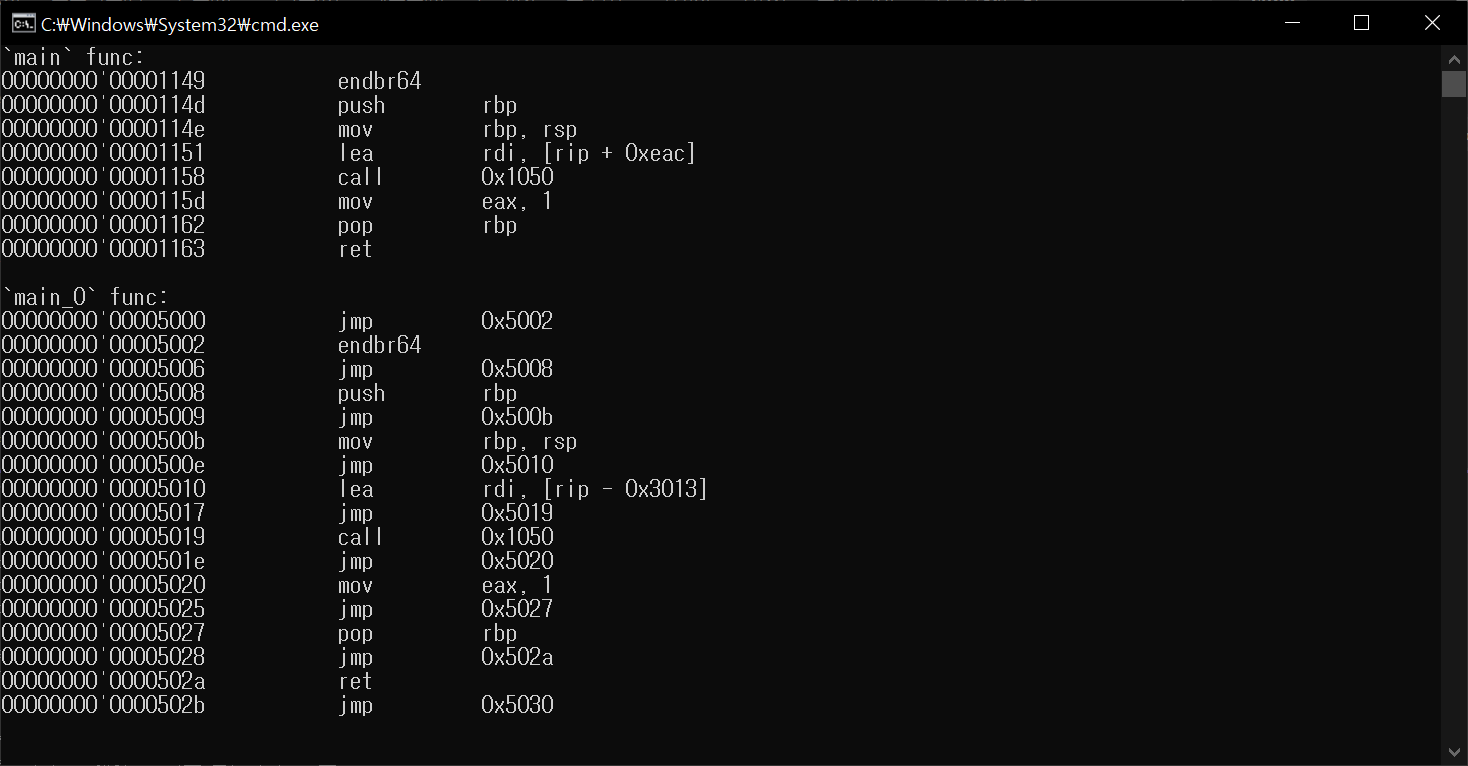
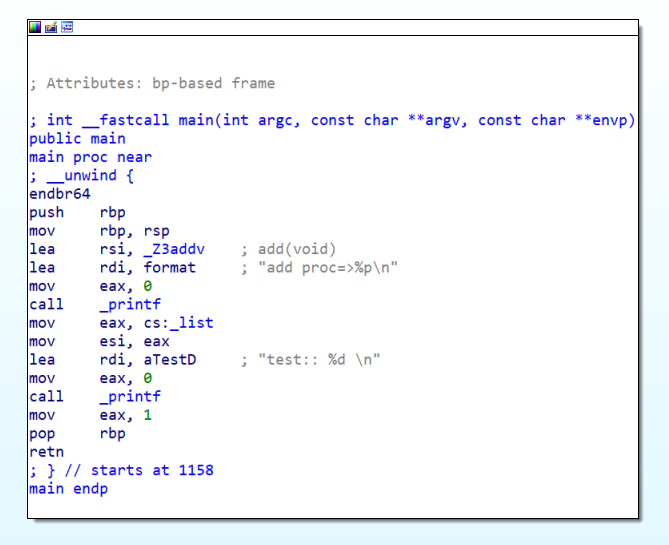
ELF 5. Disassemble `main` func
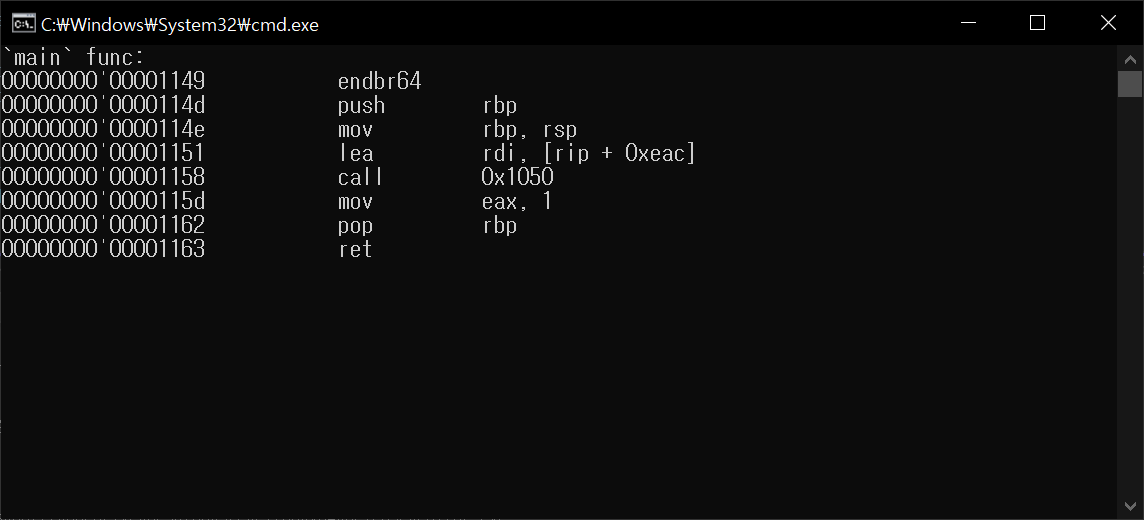
ELF 6. Simple Obfuscation `main` func
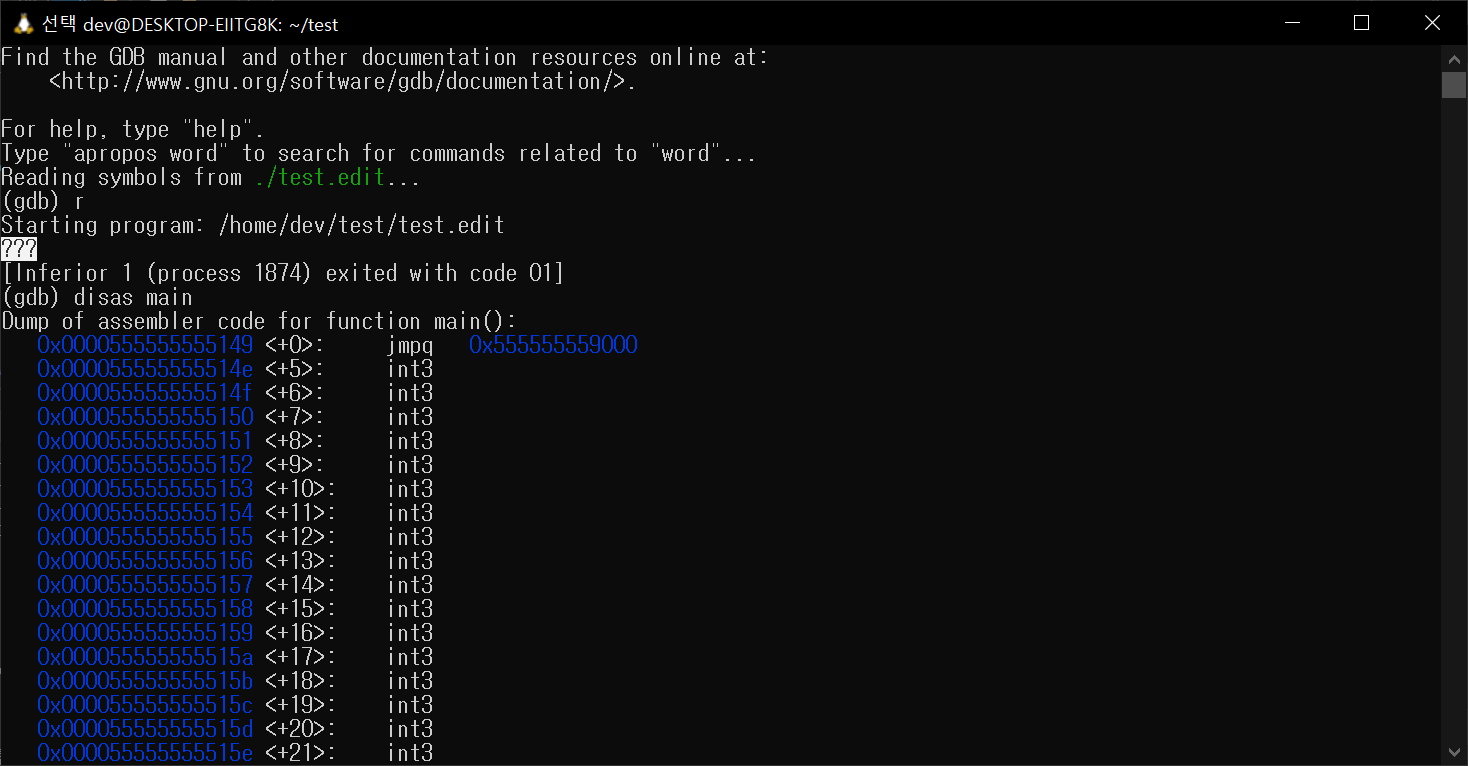
[2024.09.30.update]
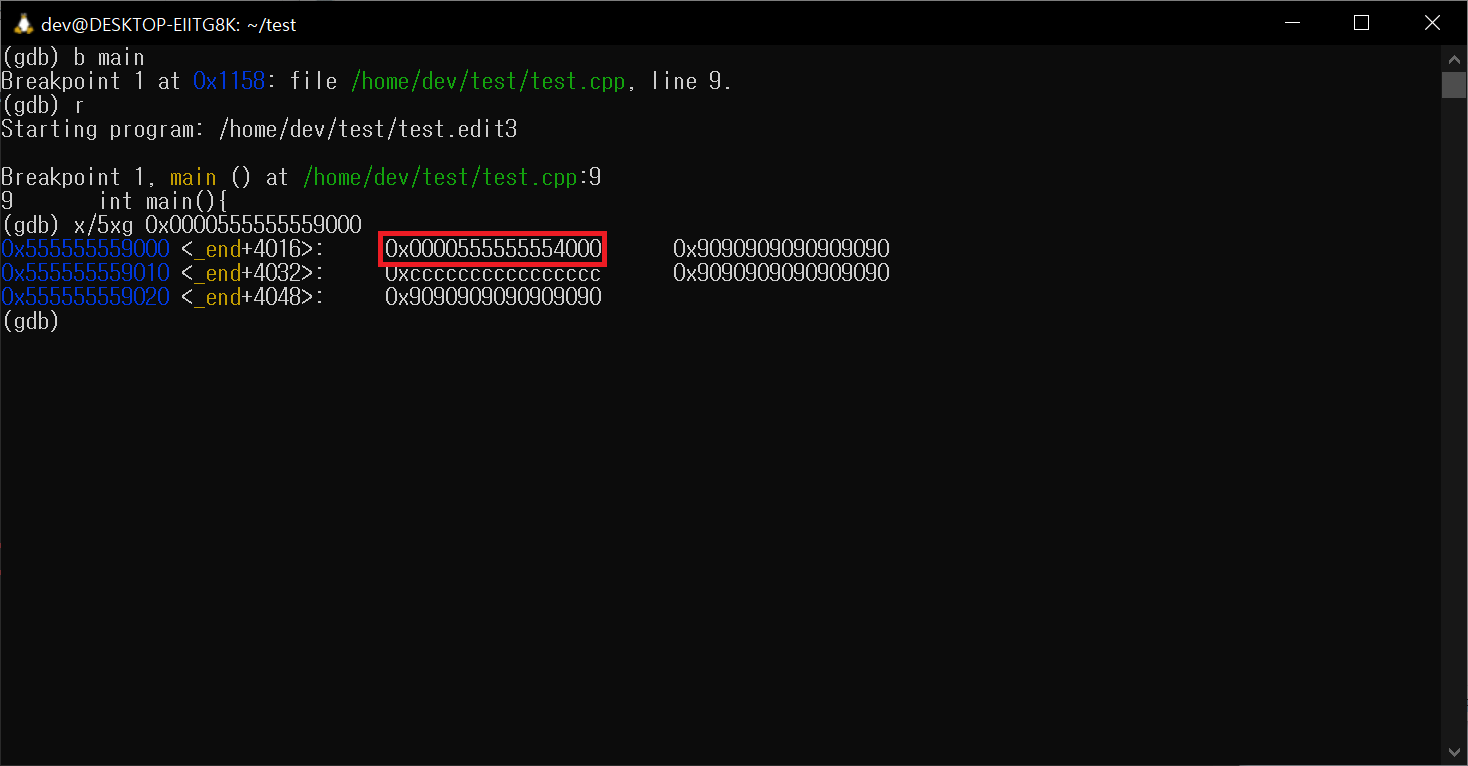
VxLang can now easily manipulate ELF relocation data.
ELF 6. Before the patch
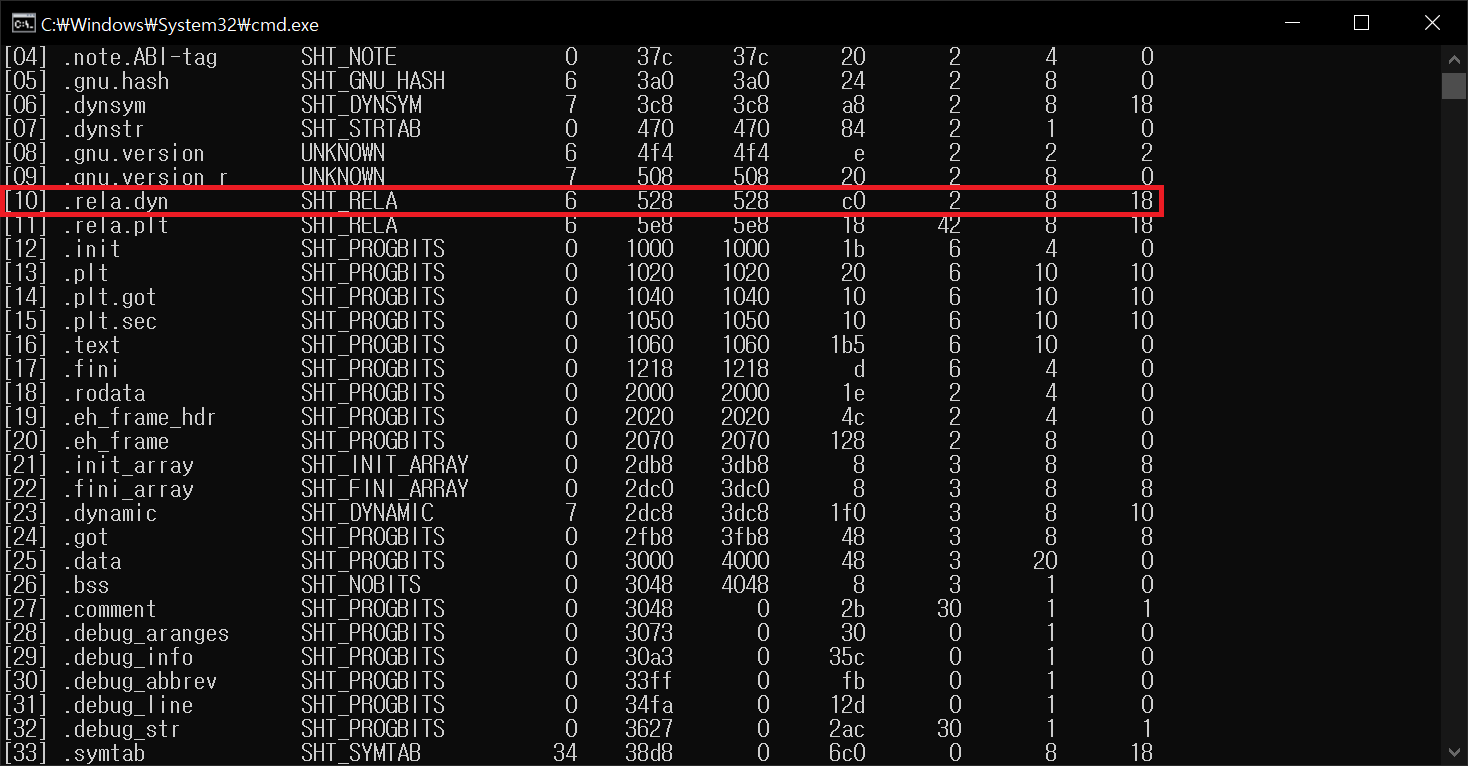
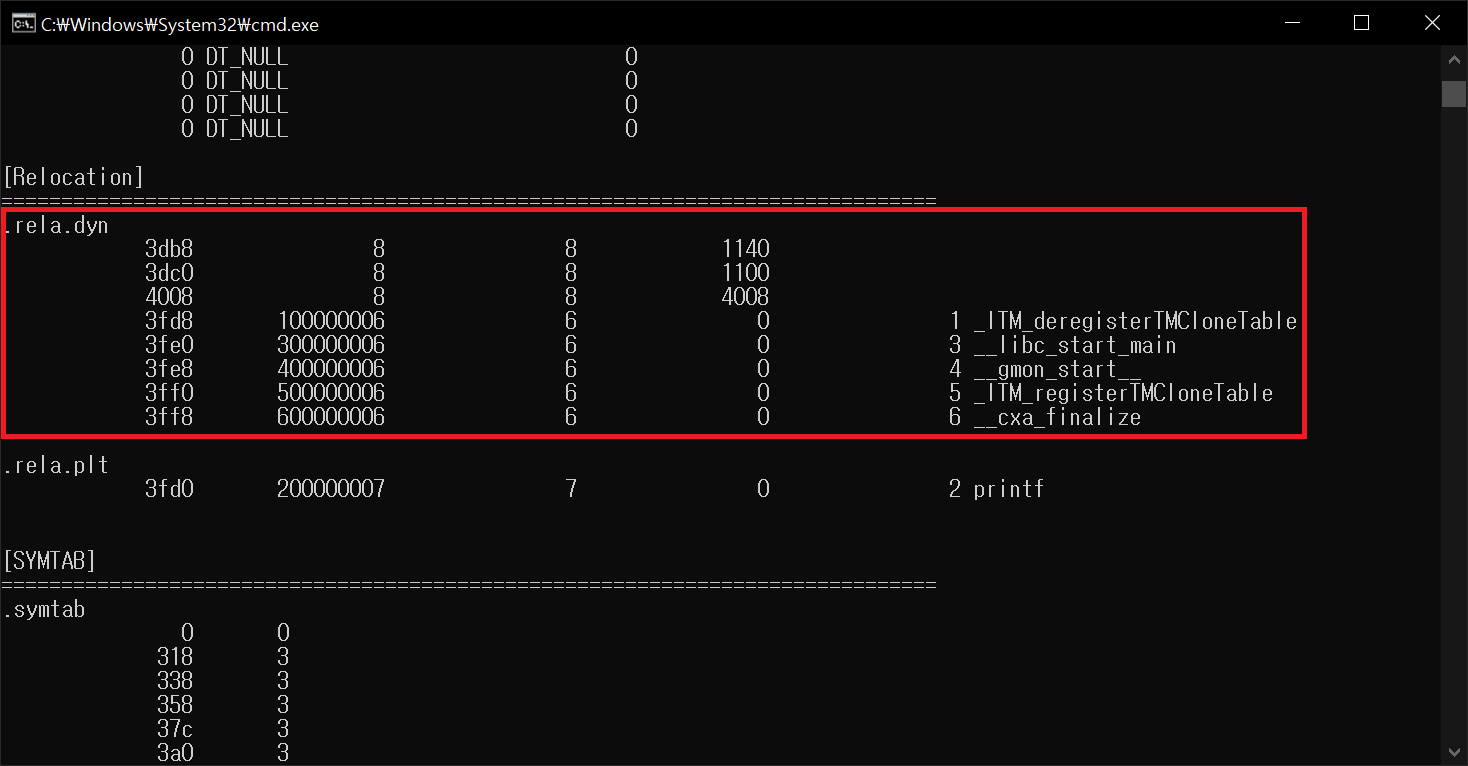
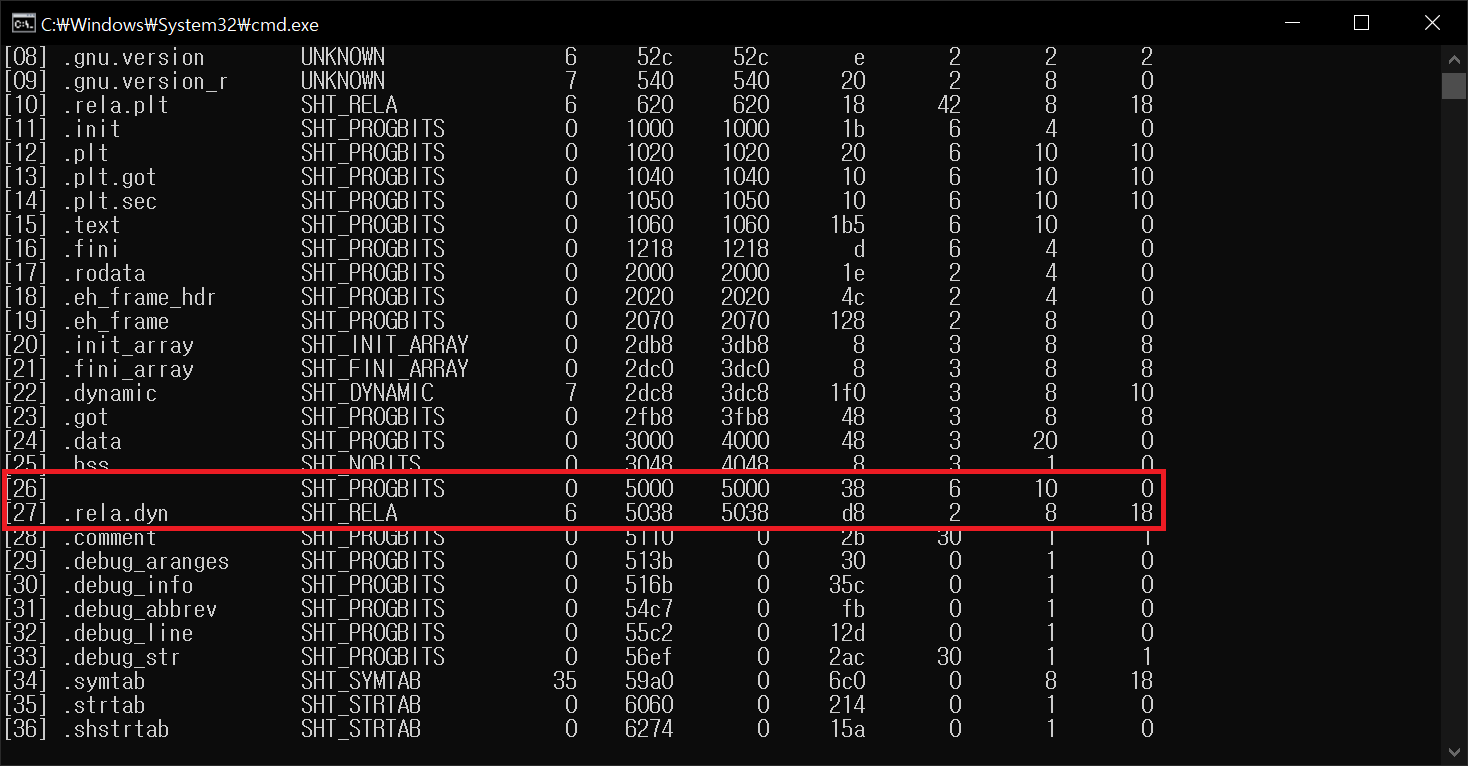
ELF 7. Patching ELF Relocation Data
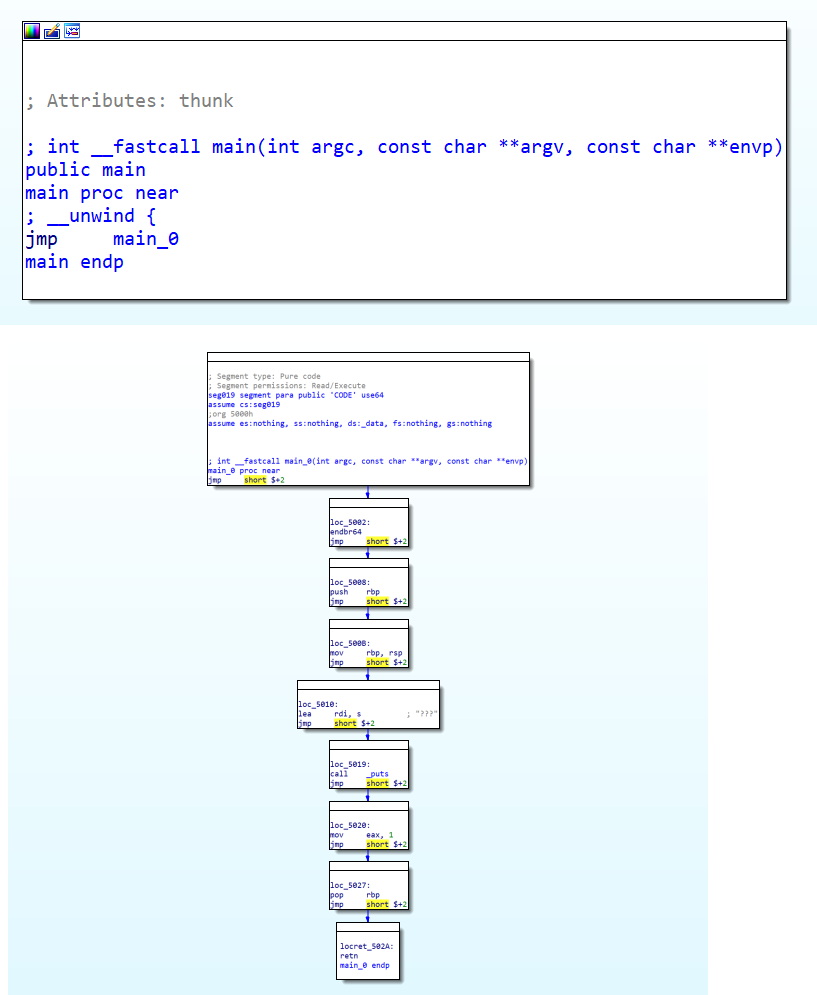
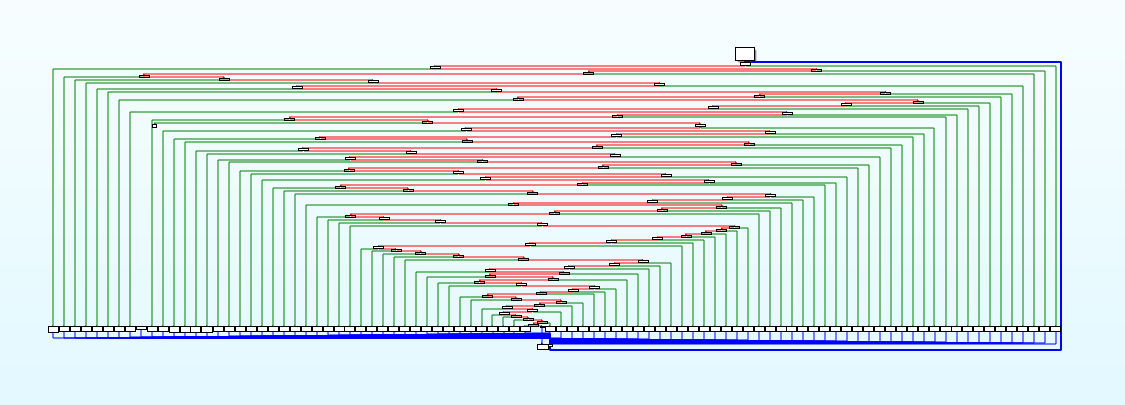
ELF 8. `main` func flattening
(I will be adding ELF code obfuscation first, followed by ELF packer, then COFF code obfuscation.)
ELF 0. SRC File

ELF 1. Added Segments

ELF 2. Added Sections

ELF 3. Check Segment and Sections(; image dump sections)

ELF 4. Check Section Data

[2024.09.22.update]
I added a disassembler for elf-format, and now I can compute the function to be obfuscated via SDK or symbols.
Now, i'm started porting the code obfuscation tools.
---
ELF 5. Disassemble `main` func

ELF 6. Simple Obfuscation `main` func



[2024.09.30.update]
VxLang can now easily manipulate ELF relocation data.
ELF 6. Before the patch


ELF 7. Patching ELF Relocation Data



ELF 8. `main` func flattening




News
1.7.4.0
- Windows Version Patch
- Fixed a bug that prevented SEH processing during function unit obfuscation.
- Fixed all obfuscation entry points to be virtualized.
1.7.3.0
- Windows Version Patch
- PDB/MAP related bug fixes
- Fixed bug with virtualize/obfuscate specification
- Fixed bug with nested obfuscation
1.7.2.0
- Windows Version Patch
- Added support for `Tail Call Optimization (TCO)`
- Fixed VM compilation bug for `SDK call-link`
- Fixed Packer bug
-
If SDK-End is a `jump-link`, returns.
-
SDK flag issues, clang/gcc/rust/etc.
-
Resource table issues
1.7.1.0
- Windows Version Patch
- Fixed a bug where enabling the `reflection` option caused a conflict with `vxlang-link-event`.
- Fixed to allow loading of extension modules even if their section alignment value is not 0x10000.
-
In such cases, testing and updates are planned to exception handling and TLS settings for extension modules.
1.7.0.0
Added beta code for the ELF file format.
- The beta version only supports general code flattening.
- Beta features require users to specify target code.
- VxLang recommends using the `-fno-pic` option in ELF 32bit binary builds.
- The beta version only supports general code flattening.
- Beta features require users to specify target code.
- VxLang recommends using the `-fno-pic` option in ELF 32bit binary builds.
A sample usage is shown below:
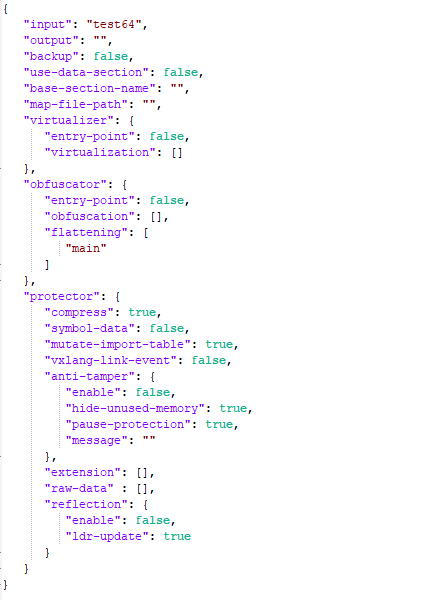

1.6.9.0
Fixed extension module load timing, now loads faster than before.
Fixed Critical bug.
From now on, the general obfuscation/flattening technique will also have handlers added to specific commands.
1.6.8.0
A new CFG has been added to the code flattening process.
I was able to add this method because the branch table setting is now available in the VxLang internal x86-64 assembler.
This method is randomized with the existing method.
Binary expiration is extended to the end of October.

From now on, the general obfuscation/flattening technique will also have handlers added to specific commands.
1.6.7.0
Fixed bug where obfuscation patterns were not applied randomly.
Updated License-File.